Cybersecurity is often ignored by many organizations as it is frequently overlooked for other business priorities that hoard the company budget. In fact in 2020, a study by Thales found that 50% of organizations spent just 6-15% of their security budget on data security. It is crucial to ensure the storage of data is protected, updated and monitored accordingly to validate the effectiveness of the organization’s business operations. This can be done with a robust cybersecurity risk management system.
Generally, the management system involves FOUR (IACR) stages:
- Identifying risk – evaluating the organization’s structure to identify the current or potential risks that could affect business operations.
- Assessing risk – analyzing the identified risks to see how it impacts the organization.
- Control risk – provide methods, procedures, technologies, or other measures that can help the organization to mitigate the risks.
- Review controls – continuously evaluating the systems are producing the desired results at mitigating risks and adding or adjusting controls as needed.
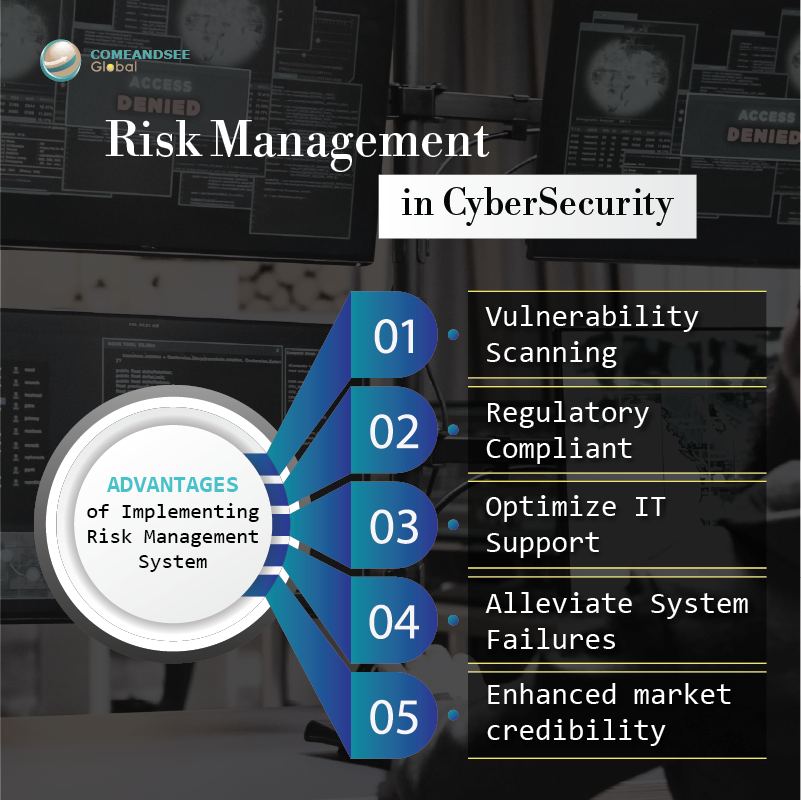
Here are some ADVANTAGES of implementing risk management system:
- Vulnerability Scanning
Vulnerabilities in the organization’s risk management system can be identified by conducting assessments. This will assist in identifying both internal and external risks and lay out the areas that are weak and need improvement. Simultaneously, it can provide guidance and elimination strategies for the system.
- Regulatory Compliance
Failure to comply with the government-mandated requirements and regulations often leave organizations at risk of being fined. Risk management systems will assist in identifying exactly where the areas that are in non-compliance, provide solutions to alleviate the issue and hence ensuring that penalties are avoided.
- Optimize IT Support
Having an efficient cybersecurity risk management system lessens the load of the IT department as it provides solutions through the software. Therefore, ensuring that the risk management system responds to the emerging crisis and automatically follows a set of protocols accordingly is essential.
- Alleviate System Failures
A cyber-attack may result in hours of downtime, bringing down the productivity levels of employees and disrupting services for clients. Having a solid cybersecurity risk management system will assist in minimizing such issues.
- Enhanced market credibility
An organization’s reputation can be protected with an efficient risk management system. For instance, a data breach may result in significant capital losses and reputational damage. Such attacks make it almost impossible to regain a client’s trust and loyalty. With a cybersecurity risk management system, it is possible to mitigate a cyber-attack successfully, and keep client’s data protected. In 2022, according to Gartner, 56% of customers have expressed “frequent interest and concern” in the cybersecurity of the organizations that they do business with.
Although cyber threats will continue to pose a risk, having a well-built cybersecurity risk management system is not only a great way to protect the organization but also continuously validates the effectiveness of its business operations.